In this blog post, we will be going through the networking overview of the Azure Landing Zone.
Networking Decision Guide
The below network decision tree should be used as a starting point to determine the network services that should be used.
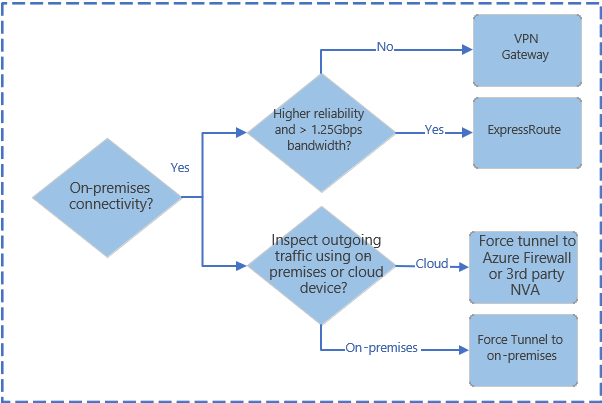



Consider the following design elements:
Below are the design consideration for Azure networking and connectivity.
- Planning for IP Addressing
- Configure DNS
- Define an Azure Networking Topology
- Connectivity to Azure
- Connectivity to other cloud providers
Planning for IP Addressing
IP address planning is a vital first step when designing a network in Azure especially if you have a hybrid environment to avoid overlapping IP address space across on-premises environment and Azure.
Design Considerations:
- Azure reserves 5 IP address with each subnet so factor in the address space when sizing the virtual networks.
- Some Azure service such as Application Gateway – WAF, Azure Firewall, Azure Bastion and VPN Gateway require dedicated subnets.
- You can delegate subnets to some Azure service that can be injected into the virtual network.
Design Recommendation:
- IP address space should not overlap the on-premises environment.
- Use the non-routable, private address spaces.
- 10.0.0.0 – 10.255.255.255 (10/8 prefix)
- 172.16.0.0 – 172.31.255.255 (172.16/12 prefix)
- 192.168.0.0 – 192.168.255.255 (192.168/16 prefix)
- You cannot add the following address ranges:
- 224.0.0.0/4 (Multicast)
- 255.255.255.255/32 (Broadcast)
- 127.0.0.0/8 (Loopback)
- 169.254.0.0/16 (Link-local)
- 168.63.129.16/32 (Internal DNS)
- Plan for future growth since adding address space can cause an outage.
- Public IP addresses should not be used for virtual networks.
Domain Name System (DNS)
Since DNS is a critical part of networking, some companies may use their exisiting DNS solution and other may adopt native Azure capabilities.
Design Considerations:
- The maximum number of private DNS zone, which can be linked to a virtual network with auto-registration is one.
- Be aware of the Azure Private DNS zone limits.
Design Recommendation:
- Use Azure DNS zones for Azure related name space resolutions.
- In a mix environment (Azure + on-premises environment), use exiting DNS services such as Active Directory integrated DNS.
- If the Azure environment is running Azure Firewall, then DNS Proxy should be evaluated.
Azure Networking Topology
Azure Virtual WAN is a Microsoft managed solution that provided end to end global and dynamic transit connectivity.
Virtual WAN simplifies end to end network connectivity from on-premises to Azure and within Azure by creating a hub and spoke network architecture.
Virtual WAN network topology.

A traditional Azure network topology.

Connectivity to Azure
Design Considerations:
- Azure ExpressRoute private connectivity to Azure infrastructure since the traffic is not going through the internet.
- Private Link can be established for connectivity to Azure platform as a service (PaaS) over ExpressRoute with private peering.
Design Recommendation:
- ExpressRoute should be used as the primary connection for connecting an on-premises environment to Azure. Furthermore, site to site VPN can be used as a backup connectivity.
- Using a single ExpressRoute connection is the singe point of failure so use dual ExpressRoute circuits.
- ExpressRoute/VPN Gateway come in various SKUs so choose the right SKU based on the requirements.
Connectivity to other cloud providers
Follow the below cross-cloud connectivity flow chart for choosing an option.
Option 1 – Customer manages routing.
Option 2 – A cloud exchange provider manages routing.
Option 3 – Use site to site VPN.

Design Considerations:
- Azure virtual network can only be connected to another cloud provider’s virtual private cloud (VPC) if the private IP addresses do not overlap.
- Site to site VPN have lower throughput and higher latency than ExpressRoute.
- Design Recommendation:
- If you do not want to use public internet, then choose option 1 and 2.
- If ExpressRoute is not available, you can use site to site VPN with traffic going through the internet for the connection between Azure and cloud provider.
This wraps up the Azure Landing Zone – Networking Overview.

Very well done Abdul ! Thanks for sharing.